• Web
Ripping
• Google
Hacking
• SQL
Injection
• PHP
Remote Code Execution
• Cross
Site Scripting
• Directory Transversal Attacks
THIS IS FOR EDUCATIONAL PURPOSE ONLY, I AM NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY VISITORS, THIS IS FOR ETHICAL PURPOSE ONLY
Web Ripping:
• Web
Ripping is finding and extracting pictures and other media files from specified
website URLs and save them to your hard drive.
• Web
Ripping is the ability to copy the structure of a Web site to a local disk and
obtain a complete profile of the site and all its files and links.
• We can use Black Windows Web ripper for
web ripping.
Google Hacking:
•
As we all know, Google is a Search Engine.
• Google keeps snapshots of
pages it has crawled that we can access via the Cached
link on the search results page.
• Google
hacking involves using Advance Search Operators in the Google search engine to
locate specific strings of text within search results. Some of the more popular
examples are finding specific versions of Vulnerable Web Applications.
• You can
look for the particular File types, Password files and Directories. Even you
can find out the IP based CCTV Cameras.
Intitle: Search For the Text In The title of the websites
This Search
This Search
will give you the List of all the websites with Title Hacking
This Search
will give you the List of all the website link containing the MS Word Document
of the name hacking.
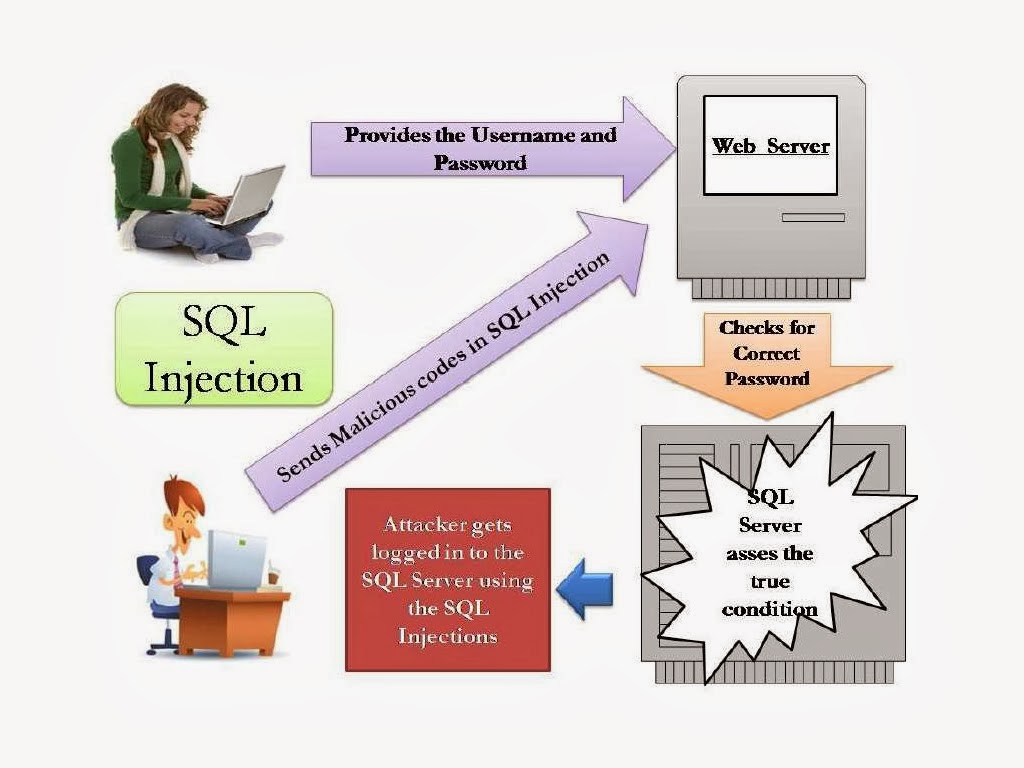
SQL
Injection:
•
A SQL injection attack exploits vulnerabilities in a web server database that
allow the attacker to gain access to the database and read, modify, or delete
information.
•
An example of a SQL injection attack is making the condition true by giving the
identical value to a web page. These values can be inserted into a login as
follows:
•
Login: 1' or '1'='1 and Password= 1' or '1'='1
•
Login: 1' or '1'='1';--
•
When the Username argument is evaluated, ‘1’=’1’ will assess to TRUE, and an
authentic username will be returned. The Systematic Execution of SQL injection
is explained in the image below
Input
validation on the SQL Injection:
•
There are measures that can be applied to mitigate SQL injection attacks.
•
Web developer can check whether some suspicious characters are sent from the
Login Page like ‘,
“,
;,
-- ,
etc
•
Always store the Passwords in the Database server in the Encrypted Form.
•
Use of these practices does not guarantee that SQL injection can be completely
eliminated, but they will make it more difficult for Hackers to conduct these
attacks.
Input Validation can help prevent :
PHP
Injection: Placing PHP backdoors:
This attack
provides the means for a Hacker to execute his or her system level code on a
target web server. With this capability, an attacker can compromise the web
server and access files with the same rights as the server system software.
• For
example, a number of PHP programs contain a vulnerability that could enable the
transfer of unchecked user commands to the eval ( ) function.
So what is PHP Eval() function:
PHP
Remote code Execution:
How
Attackers Hide Them While Attacking:
Proxy Servers
• A Proxy
Server is a server that acts as an intermediary between a workstation user and
the Internet so that the enterprise can ensure security, administrative control
and caching service.
• Hackers
generally use the Proxy server on the Internet to make their Identity invisible
to the target.
• So They
hide their IP address by using the proxy server and make an anonymous brousing
over internet.
• Please
See the diagram for better understanding.
Types
of Proxy Servers
•
Web Proxy
•
Anonymous Proxy Server
Web
Proxy Server
•
A Proxy site is a web page which allows a user to browse other web sites.
•
If an Attacker finds that he is blocked from accessing a Website, he will use
any of web proxy sites to get bypass the block.

Types
of Proxy Servers
•
Web Proxy
•
Anonymous Proxy Server
Web
Proxy Server
•
A Proxy site is a web page which allows a user to browse other web sites.
•
If an Attacker finds that he is blocked from accessing a Website, he will use
any of web proxy sites to get bypass the block.
“Do not use
this hack trick in any criminal activities and please do not destroy any ones
account
this is for
educational purpose only”.
========== Hacking Don't Need Agreements ==========
Just Remember One Thing You Don't Need To Seek Anyone's Permission To Hack Anything Or Anyone As Long As It Is Ethical, This Is The Main Principle Of Hacking Dream
Thank You for Reading My Post, I Hope It Will Be Useful For You
I Will Be Very Happy To Help You So For Queries or Any Problem Comment Below Or You Can Mail Me At BhanuHacks@gmail.com













No comments:
Post a Comment