THIS IS FOR EDUCATIONAL PURPOSE ONLY, I AM NOT RESPONSIBLE FOR ANY ILLEGAL ACTIVITIES DONE BY VISITORS, THIS IS FOR ETHICAL PURPOSE ONLY

1.
Wireless network
refers to any type of computer network which is wireless, and is commonly
associated with a network whose interconnections between nodes e.g. Laptops,
Desktops, Printers etc is implemented without the use of wires.
2 2.
The popularity in
Wireless Technology is driven by two major factors: convenience and cost. A
Wireless Local Area Network (WLAN) allows workers to access digital resources
without being locked to their desks. Mobile users can connect to a Local Area
Network (LAN) through a Wireless (Radio) connection.
3.
Demand for wireless
access to LANs is fueled by the growth of mobile computing devices, such as
laptops and personal digital assistants, and by users’ desire for continuous
network connections without physically having to plug into wired systems.
4.
For the same reason
that WLANs are convenient, their open broadcast infrastructure, they are
extremely vulnerable to intrusion and exploitation. Adding a wireless network
to an organization’s internal LAN may open a backdoor to the existing wired
network.
5.
The IEEE 802.11
standard refers to a family of specifications for wireless local area networks
(WLANs) developed by a working group of the Institute of Electrical and
Electronics Engineers (IEEE).
6.
This standards effort began in 1989, with the focus
on deployment in large enterprise networking environments, effectively a
wireless equivalent to Ethernet. The IEEE accepted the specification in 1997. Standard
802.11 specifies an over-the-air interface between a mobile device wireless client
and a base station or between two mobile device wireless clients.
Wireless
Standards:
• WAP (Wireless Access Point):
Wireless
Access Point is the point from where the Wireless network are generated. Like
the Wireless Routers or Switches.
•SSID (Service Set Identifier):
An
SSID is the name of a wireless local area network (WLAN). All wireless devices
on a WLAN must employ the same SSID in order to communicate with each other.
SSID is also known as ESSID (Extended Service Set Identifier).
• BSSID (Basic Service Set Identifier):
A
BSSID is the MAC Address (Media Access Control) or Physical Address of the
Wireless Access Point or the Wireles Router. This is a unique 48 bit key
provided by the manufacturer of the device. It can be in the form of
Hexadecimal
i.e.
0-9 , A-F.
E.g. 00:A1:CB:12:54:9F
• For checking your card’s MAC Address:
Start
> Run > CMD
Write
“getmac”
in Command Prompt.
•
Beacons:
These are
the Wireless Packets which are broadcasted to maintain the connectivity with
the Wireless Access Point and Client systems. The Wireless Access point
broadcasts beacon frames from time to time to check connectivity with the
systems.
•
Channel:
It is the
frequency at with the Wireless Signal travels through air.
•
Data Packets:
These are
the packets which sent and received for the transfer of data between Wireless
Access Point and Client systems. All the data communicated between two Computers
travels in the form of Data Packets.
•
Data Packets:
These are
the packets which sent and received for the transfer of data between Wireless
Access Point and Client systems. All the data communicated between two
Computers travels in the form of Data Packets
SSID
Solution:
Wireless
equipment manufacturers use a default Service Set ID (SSID) in order to
identify the network to wireless clients. All access points often broadcast the
SSID in order to provide clients with a list of networks to be accessed.
Unfortunately, this serves to let potential intruders identify the network they
wish to attack. If the SSID is set to the default manufacturer setting it often
means that the additional configuration settings (such as passwords) are at
their defaults as well.
Good
security policy is to disable SSID broadcasting entirely. If a network listing
is a requirement for network users then changing the SSID to something other
than the default, that does not identify the company or location, is a must. Be
sure to change all other default settings as well to reduce the risk of a
successful attack.
MAC
address filtering:
Some 802.11
access point devices have the ability to restrict access to only those devices
that are aware of a specific identification value, such as a MAC address. Some
access point devices also allow for a table of permitted and denied MAC
addresses, which would allow a device administrator to specify the exact remote
devices that are authorized to make use of the wireless service. Client
computers are identified by a unique MAC address of its IEEE 802.11 network
card. To secure an access point using MAC address filtering, each access point
must have a list of authorized client MAC address in its access control list
We can
Prevent or Permit machines on the behalf of MAC Addresses
How To
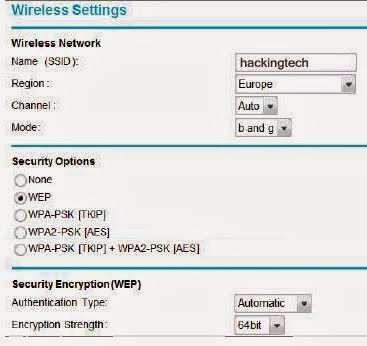
crack or hack wifi WEP Password
• Wired
Equivalent Privacy (WEP) was the first security option for 802.11 WLANs. WEP is
used to encrypt data on the WLAN and can optionally be paired with shared key
authentication to authenticate WLAN clients. WEP uses an RC4 64-bit or 128-bit
encryption key.
• WEP was
fairly quickly found to be crack able. WEP is vulnerable because of relatively
short and weak encryption. The security of the WEP algorithm can be
compromised.
Just u need
to have AIRCRACK 2.1 SOFTWARE
THERE U
HAVE TO SEARCH FOR THE WIFI THAT U WANT TO HACK AND THEN TYPE THE FOLLOWING
Very soon I
will give you much more information very clearly step by step, this is just a
sample
So please
visit frequently to get updated
Countermeasures
for Wireless attacks:
Hide the Wireless Network:
Do not
broadcast the SSID of the Wireless Network. This will help you in protecting
your
Wireless
being invisible to the people who do not know about Passive War Driving
Use a Secured Key :
You can use
the WEP Key protection on your Wireless Network to protect your Wireless
Network Connection. Although this is not the ultimate security measure but will
help you a lot against the Script
Kiddies who
do not know how to break into the WEP Protection.
WPA: Wi-Fi Protected Access
•WPA
employs the Temporal Key Integrity Protocol (TKIP)—which is a safer RC4
implementation—for data encryption and either WPA Personal or WPA Enterprise
for authentication.
•WPA
Enterprise is a more secure robust security option but relies on the creation
and more complex setup of a RADIUS server. TKIP rotates the data encryption key
to prevent the vulnerabilities of WEP and, consequently, cracking attacks.
Mac Filtering
An
early security solution in WLAN technology used MAC address filters: A network
administrator entered a list of valid MAC addresses for the systems allowed to
associate with the Wireless Access Point.
Choosing the Best Key
Always
use a long WPA Key with lower as well as upper case letters including numbers
and special characters.
Sample
Key: 12345@abcde&FGHI
========== Hacking Don't Need Agreements ==========
Just Remember One Thing You Don't Need To Seek Anyone's Permission To Hack Anything Or Anyone As Long As It Is Ethical, This Is The Main Principle Of Hacking Dream
Thank You for Reading My Post, I Hope It Will Be Useful For You
I Will Be Very Happy To Help You So For Queries or Any Problem Comment Below Or You Can Mail Me At BhanuHacks@gmail.com







No comments:
Post a Comment